Repositorio 🦔!!!!
Mobile Security
The security of a mobile application is of utmost importance, especially today when any app can have a “MOD APK FULL 100%” (unregistered trademark). These modifications compromise the original purpose of the applications and the data of the users who use them. This, at least for me, made me reflect on what kind of things can be done with an application nowadays and how easy it can be.
It’s important to mention that although there are projects that seek to standardize analysis, like OWASP Mobile, today I believe that what I have seen the most are app modifications that offer users paid functionalities or additions for “free.”
Today’s App
Based on the above, along with a great fondness for hedgehogs 🦔 and plants 🌿⭐, it occurred to me that the best way to investigate this is to create my own application and try to attack it. Considering some good and bad practices, quite common ones, to add realism.
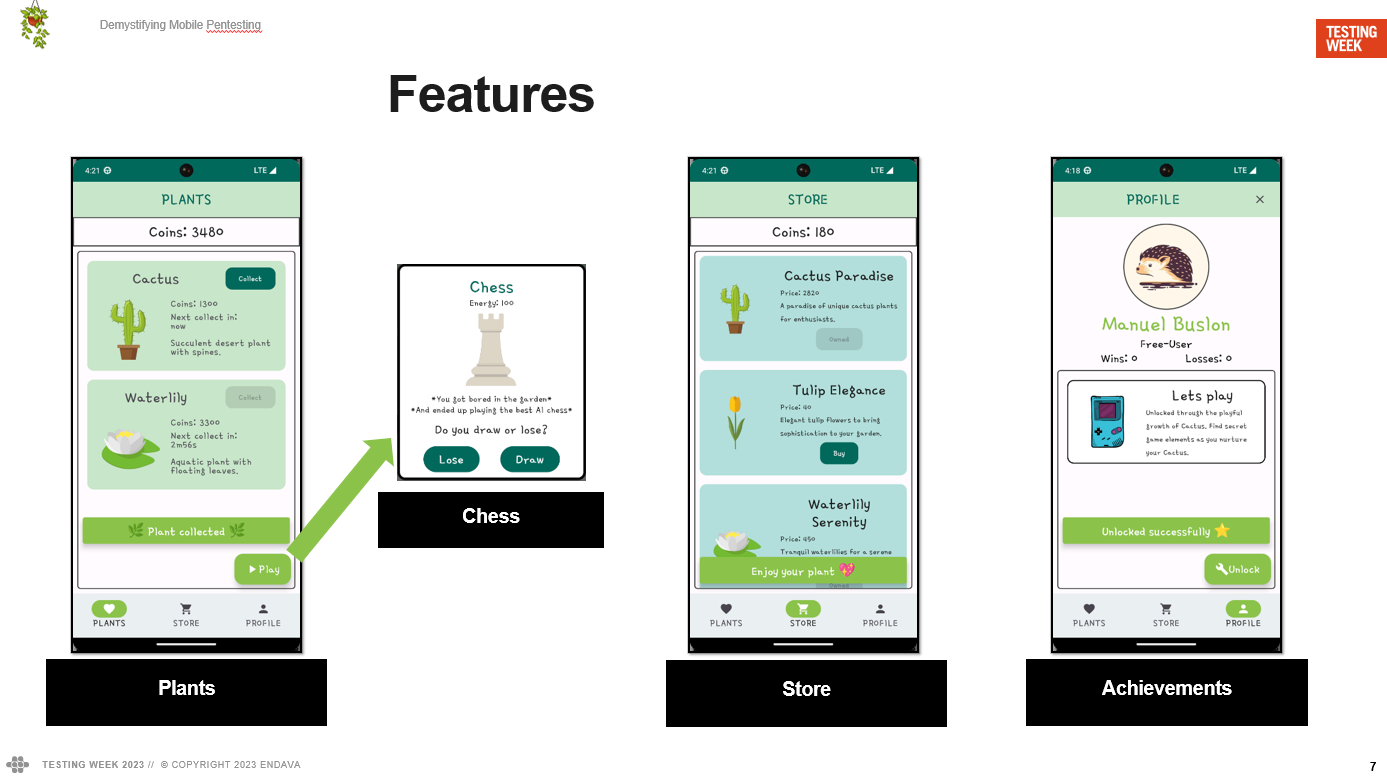
The app is called “My Enchanted Garden,” and it consists of a mobile frontend created in Kotlin using Jetpack Compose for the UI. This architectural decision was mainly made to recognize some common aspects of this UI framework and analyze if it is possible to easily modify its resulting code.

As for the backend, I decided to use Rust with PostgreSQL because I was very interested in this language at the time, and it seemed like a correct option if I planned to dedicate time and effort. I didn’t want to end up using JS…

The app consists of a garden of plants that can be harvested at certain intervals to obtain coins. Those coins can be used in the store to buy more plants and get more. Additionally, it has a small “chess” mini-game that offers outcome options for the game. Obviously, for non-premium users, the game does not offer the option to win.
Finally, it also includes an option in the profile to unlock achievements using codes, which are completely secret and the user will obtain them at some point while playing.
In the following sections, we will see more details, but really, with enough work, ALMOST anything can be changed in the client; it’s a matter of how much time you have to analyze and test.
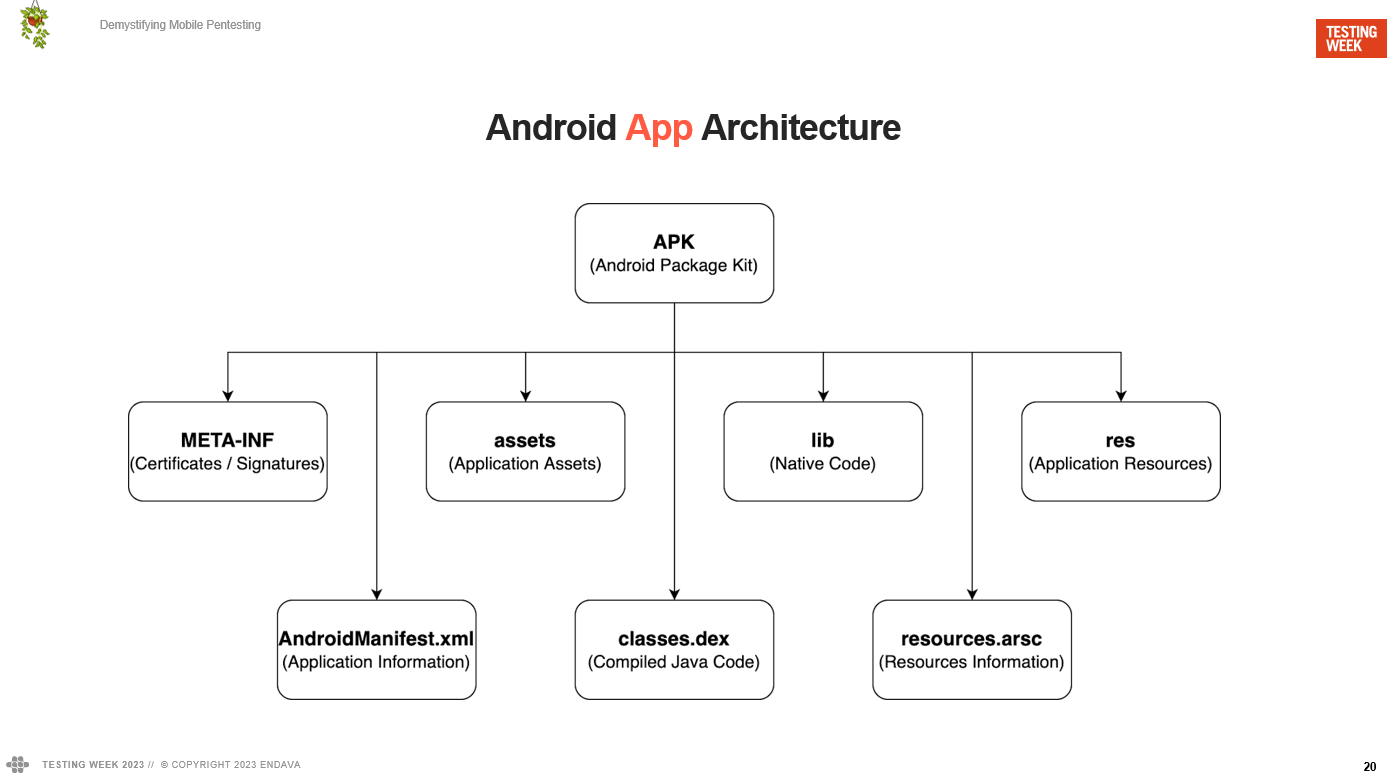
APK
Continuing with the main objective, to start analyzing and then modifying the application, we first need to understand the architecture of a mobile application package.
Broadly, it consists of the following:
- METE-INF:
Certificates and signatures. Broadly speaking, due to these signatures, we cannot install a mod having the original application. - AndroidManifest.xml:
This file contains information about the application, its main screens, services, permissions, and more. - assets:
These are the application’s assets, such as the icons it uses. - classes.dex:
Consists of the application code written in Java or Kotlin. This is modified during compilation to create an optimized format. - lib:
Here are the libraries that the app uses. In our case, there won’t be any. - resources.arsc:
Compiled resource file. - res:
Directory with uncompiled resources.
Tools
So far, I have mainly used two tools for analysis and modification: Jadx and Frida. Although they are quite useful, both require some experience to read, understand, and create scripts, but they are highly recommended.
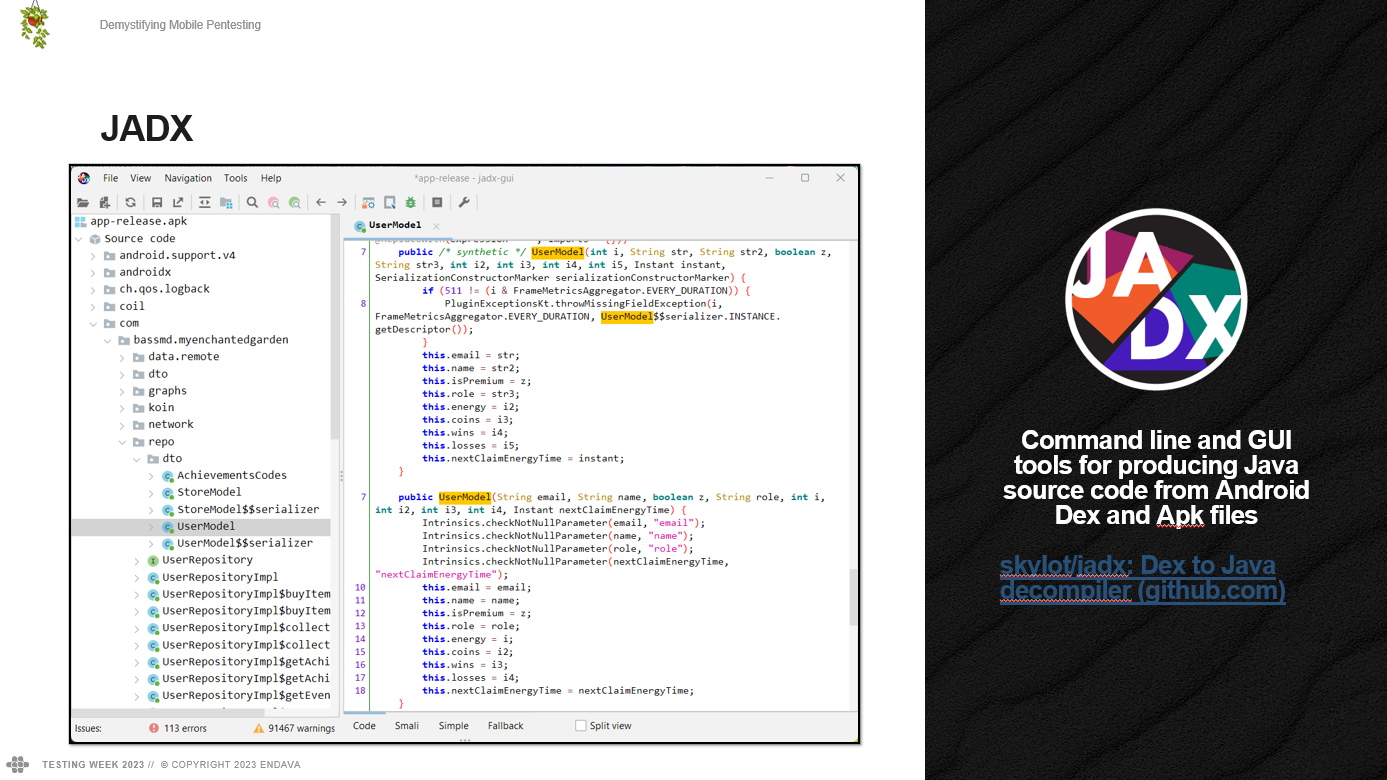
JADX
Jadx is a popular tool for reverse engineering Android applications. It allows us to decompile APK files and obtain the source code in Java, which is very useful for analyzing the application’s behavior and looking for potential vulnerabilities.
More about this tool will be explored in another post
Frida
Frida is a powerful dynamic instrumentation tool. It allows injecting scripts into applications at runtime, making it easier to analyze and manipulate the application’s behavior without the need to modify the APK.
The injection process can be appreciated more in the Python script created for this purpose, in addition to observing the code of the shown modifications and some more.
Script 🦔!!!!
More about this tool will be explored in another post
Reversing
Next, we will explore some of the examples designed and executed in the repository.
Hedgehogs Everywhere
Imagine a pirate hedgehog looking to modify our app to show the image they want or alter the rendering behavior of Jetpack Compose…

Initially, what can be done to investigate the behavior of this feature is to look for a component that contains what we want.

After some time investigating in Jadx, we find the screen that contains the image, and there we observe that it uses the painter resource function.
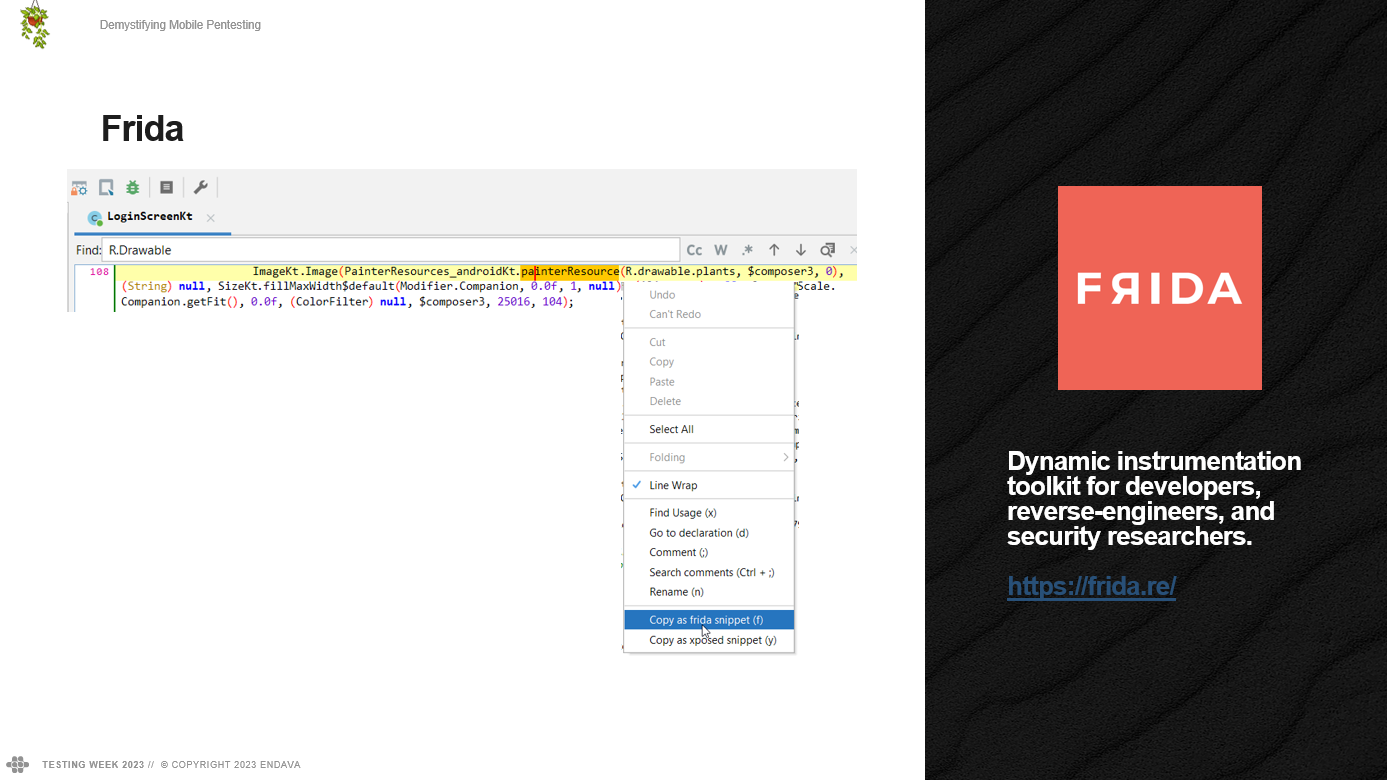
Then we can copy it as a Frida snippet, observing the following:
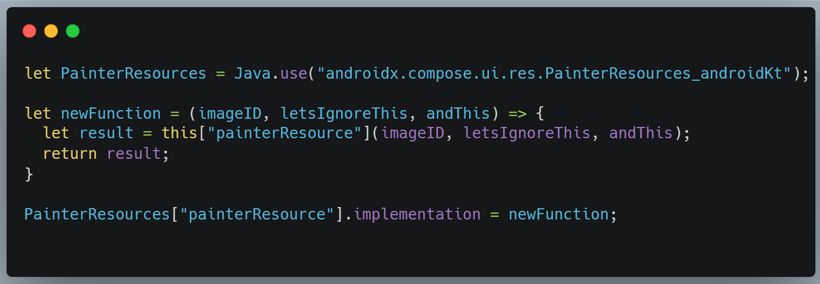
From there, we can also access the resources stored in the R class (a common class used to assign an index to each resource) and find the image to be used for the modification.
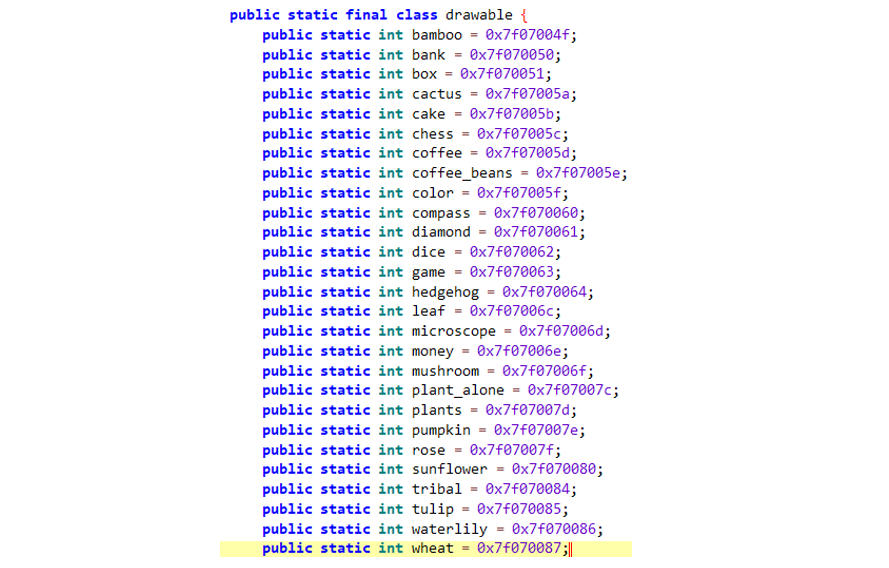
From that point, we can modify the function to always use the same image index. 🦔
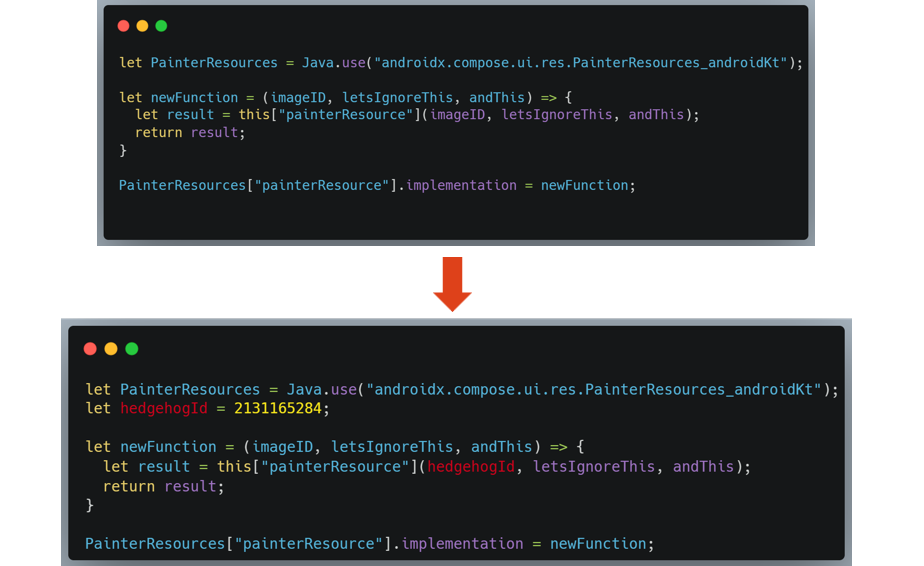
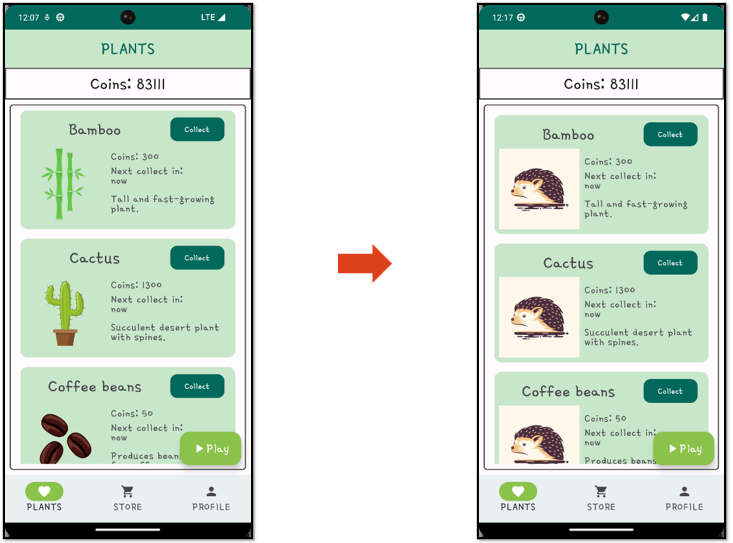
With that, the attacker gets that every image in the app now shows their hedgehog image.
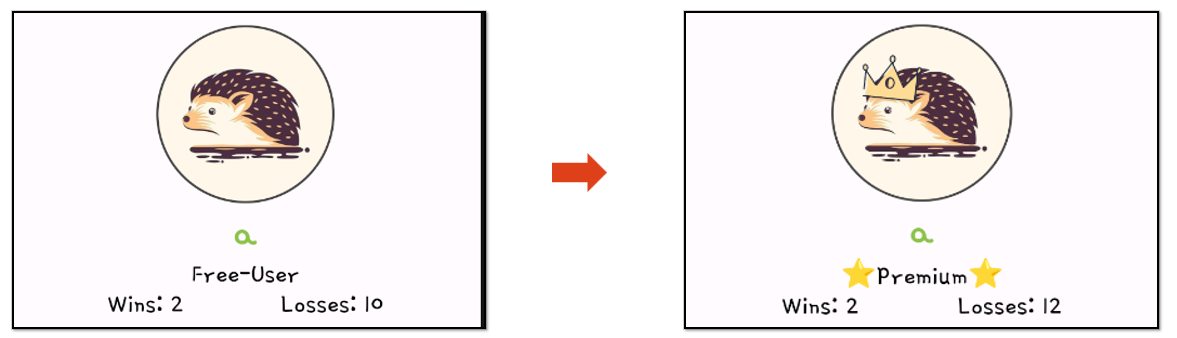
Premium
Another common point is seeking to obtain premium functionalities. In the following flow, we can observe a path to understanding how this check is handled and where the data comes from.
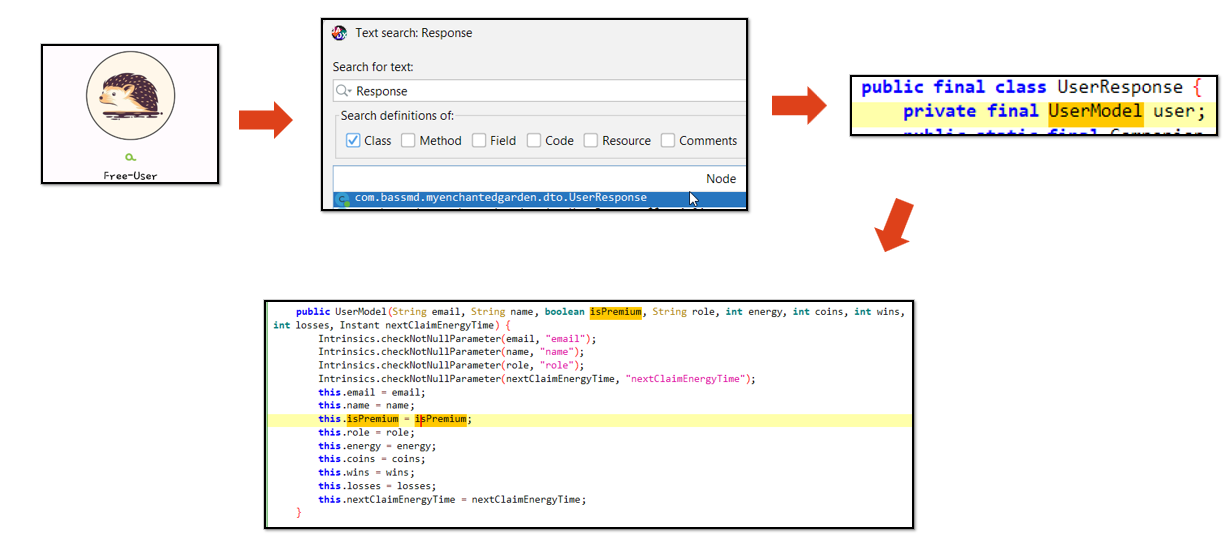
To then copy and modify the creation class code and edit it to always use “True” for premium.
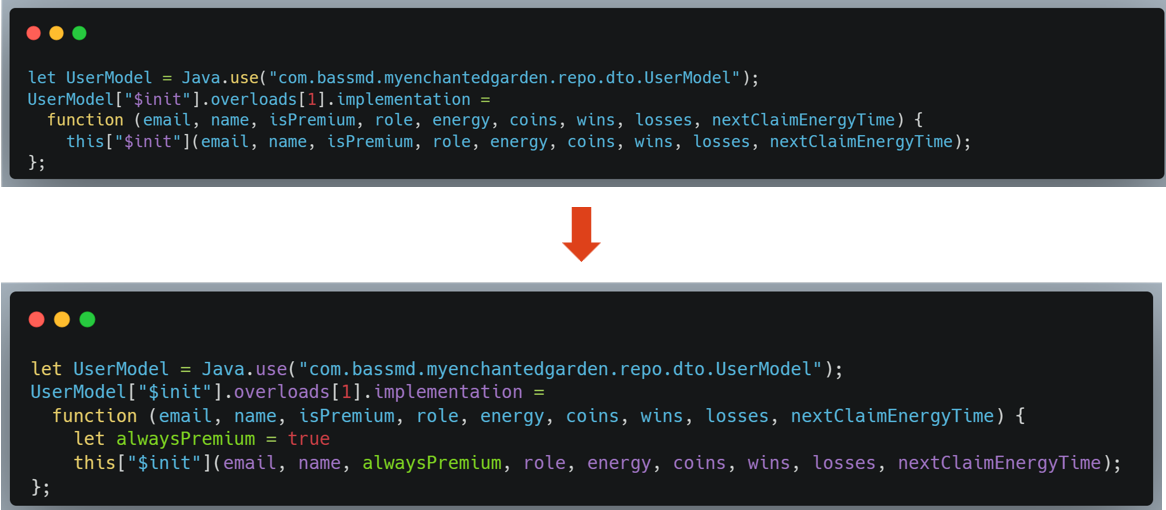
Checking the app after that change, we can verify that it works, and our hedgehog has the premium features of the app.
Another fun fact is that being premium now allows us to win in the mini-games.
Achievements
To conclude with the basic functionalities, another feature the app offers is to unlock achievements on the server with codes that the client provides to the user, as it is a local game.
By doing a bit of analysis, we can find a class with the prize codes and the function that is executed to unlock them.
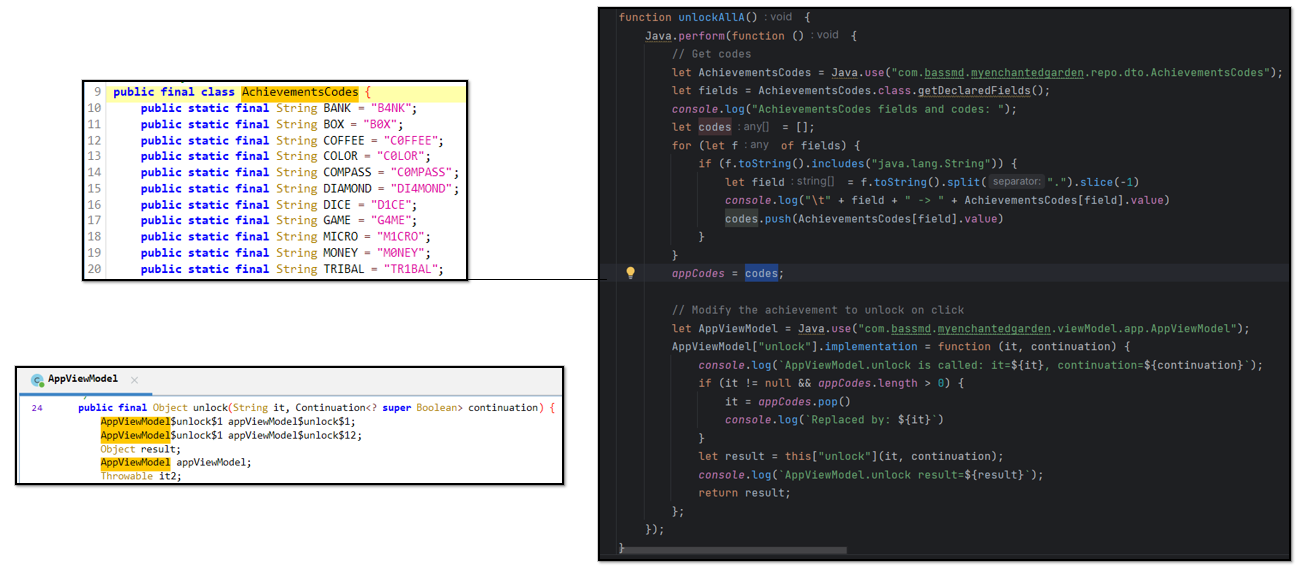
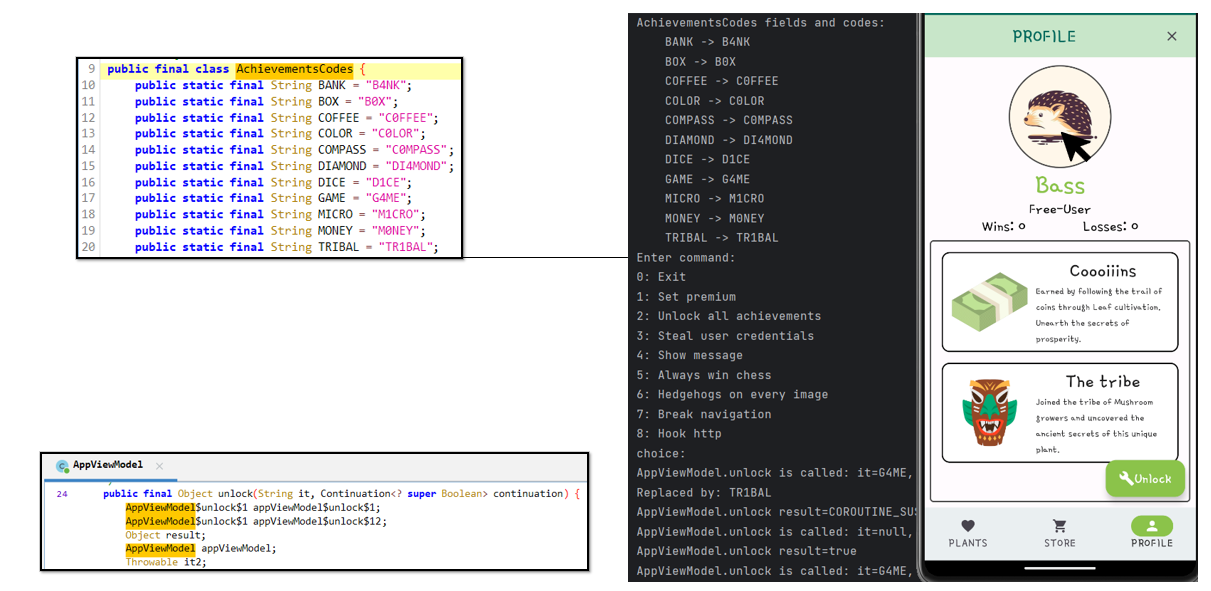
From that, as seen in the image above, we can create a script that retrieves them at runtime and sends a response to the server to unlock them all.
The previous modification is quite common and is usually offered in most app mods.
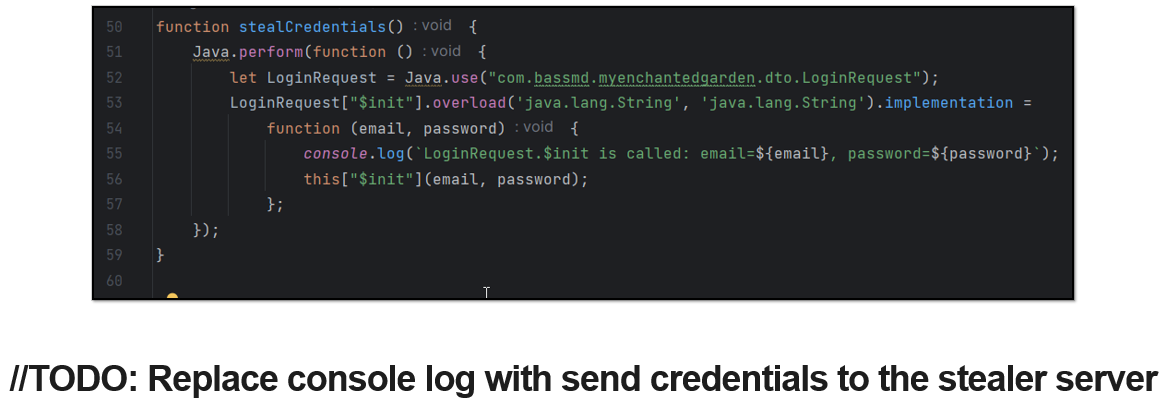
Credentials
Another type of modification that can be made, also quite common, is modifying the component of the application responsible for logging in.
From this, an attacker could offer a mod of the app and, in turn, steal the user’s credentials or session tokens..
⭐ Thank you ⭐
